
Cyberattacks in the Russia–Ukraine war
Cyberattacks in the Russia–Ukraine war. Discusses attacks before the war, ongoing cyberattacks, Ukraine’s cyberdefenses, and more.
March 16, 2022 • 5 min read
Cyberattacks in the Russia–Ukraine war. Discusses attacks before the war, ongoing cyberattacks, Ukraine’s cyberdefenses, and more.
March 16, 2022 • 5 min read
March 2022 Apple updates for macOS, iOS, iPadOS, watchOS, tvOS, and Apple software. Covers security highlights and discussion of impact.
March 15, 2022 • 4 min read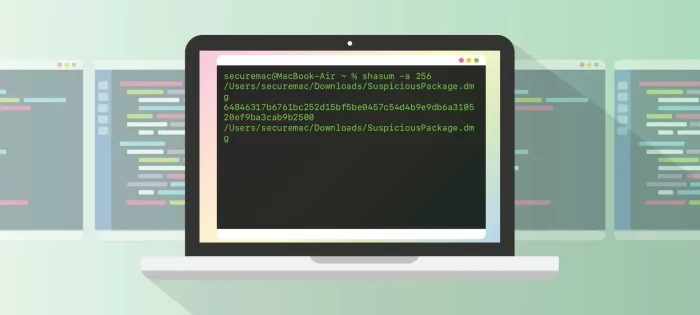
How to use checksum on Mac to verify downloads. This guide gives you the steps needed to verify a checksum in Terminal.
March 15, 2022 • 10 min read
SecureMac’s guide to Mac Trojan horse malware, updated and expanded for 2022. Covers definition, capabilities, variants, and how to avoid.
March 14, 2022 • 10 min read
Tax scams 2022: the same thing all over again? We’ll explain why old scams still work, and revisit the classic scams you need to know about.
March 11, 2022 • 2 min read
Apple Peek Performance Event highlights. Includes Mac Studio, the M1 Ultra, the new iPhone SE, the new iPad Air, and more.
March 9, 2022 • 4 min read
Ukraine relief charity scams and how to avoid them. Plus: gift card scams and how to keep your loved ones safe!
March 4, 2022 • 7 min read
Cloned AirTags and Find My security, Apple introduces new AirTag updates in iOS beta, and Google’s 2FA experiment by the numbers.
February 25, 2022 • 5 min read
Tax scams, 2022 edition. Learn what to watch out for this tax season, including SMS-based threats, unemployment fraud, and more.
February 22, 2022 • 3 min read
AirTag security updates from Apple (and plans for more in the future). Plus, helpful advice on AirTag security from New York State.
February 18, 2022 • 5 min read
How might cyberwarfare in Ukraine play out? Could it impact the rest of the world? And how can “cyber-civilians” stay safe?
February 14, 2022 • 6 min read
Apple Watch privacy tips: 6 ways to make sure your Apple Watch isn’t giving you away. Plus: Silent AirTags and how to stay safe.
February 10, 2022 • 7 min read