Mac OS X BrickHouse – The Firewall Configuration
BrickHouse (Mac OS X Firewall Configuration)
BrickHouse was developed by Brian Hill to ease the process of configuring MacOS X’s built-in Firewall.
His hard work has paid off; hundreds of OS X owners use his program. Changing Firewall settings manually without a GUI can be tedious and confusing for unexperianced users; this program removes those barriers.
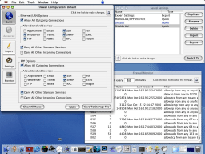
By using BrickHouse to configure your computer’s firewall, you can more effectively keep unauthorized users from gaining access to your computer via your internet connection.
BrickHouse makes it easy to use your firewall to guard against denial of service or resource-based internet attacks. Network attacks will bounce off the firewall, preventing your computer from slowing down or crashing.
BrickHouse provides a simple and easy interface to activate and configure your firewall’s filters. It also includes a firewall monitor window that allows you to see how frequently each filter is used. Filter settings can be saved and toggled quickly, and can be imported and exported to and from disk. Settings can be created by knowledgeable users and admins, who can distribute them to others, quickly disabling specific or recently discovered attack techniques.
BrickHouse includes several pre-loaded firewall filter sets for several situations, including a typical, secure set for the average home user, one that allows access to web and ftp servers, and one that allows all access from computers on a home ethernet network and no incoming access via the PPP /Internet connection.
