SecuritySecureMac has released PrivacyScan 1.5, offering privacy protection for Mac users. The latest version of the critically acclaimed personal privacy application is designed specifically for Mac OS X, adding features to securely wipe digital footprints left after using the computer and accessing the Internet. In…
January 11, 2014 •
3 min read
SecuritySecureMac has announced the release of PrivacyScan 1.4. The latest version of its critically acclaimed personal privacy application is designed specifically for Mac OS X Mavericks, adding features to securely wipe digital footprints left behind after using the computer and accessing the Internet. Because this…
November 15, 2013 •
3 min read
SecuritySecureMac’s award winning PrivacyScan software can now be downloaded in volume by schools, businesses and other organizations via the Apple Volume Purchase Program. Prior to last month, bulk purchasing software license keys was only an option for Apple software products such as GarageBand and iMovie….
November 12, 2013 •
3 min read
SecurityFor immediate release October 18, 2013Summary: SecureMac continues its work to raise awareness of online privacy issues with the release of an internet cookie infographic. The aim is educate and dispel common misunderstandings about the nature of cookies and what they mean for consumer privacy….
October 18, 2013 •
2 min read
SecurityThe links for many popular Mac apps on CNET’s download.com have been replaced with a “CNET installer” that installs toolbar adware and changes browser settings. This guide shows how to identify affected apps, how to avoid the toolbar installer, how to determine if it has…
October 13, 2013 •
4 min read
SecurityUpdate (10/29/13 12:15pm): SecureMac has prepared a guide to help users identify and remove the adware being distributed by CNET’s download.com in place of popular Mac apps. The guide provides detailed information, including step-by-step instructions to determine if the adware is installed on your system,…
October 13, 2013 •
2 min read
SecuritySecureMac has released an update to PrivacyScan that includes new support for Opera 15 and the Chromium web browser, bug fixes, an improved user interface, reduction in price and a 15-day free trial. PrivacyScan is available for a limited time for 7.99 from the Mac…
July 26, 2013 •
1 min read
SecuritySummary: SecureMac has released an update to its multiple award-winning (details below) PrivacyScan software that includes new support for Opera 15 and the Chromium web browser, bug fixes, an improved user interface, reduction in price and a 15-day free trial. As various legal debates regarding…
July 26, 2013 •
3 min read
SecurityWe’ve all heard the term ‘cookie’ used in the context of web browsers, and while we enjoy the warm, delicious connotation they bring to mind, do we really know what one is? How are cookies used by websites to provide customization and personalization? How are cookies used by third-party advertisers to track you across the internet?
July 24, 2013 •
5 min read
SecurityJune 27, 2013 – SecureMac, the leading provider in Mac OS X security and privacy, announced today that PrivacyScan 1.2 has added a new demo option and purchasing option for users. PrivacyScan, recently nominated for Best Consumer Software for the 18th Annual Macworld Awards, is…
June 27, 2013 •
3 min read
SecuritySecureMac announced today that PrivacyScan, the online and offline privacy application to seek and destroy privacy threats while clearing up valuable hard disk space, has been nominated for Macworld UK’s 2013 award in the Best Consumer Software category. PrivacyScan made the shortlist for the 18th…
June 18, 2013 •
1 min read
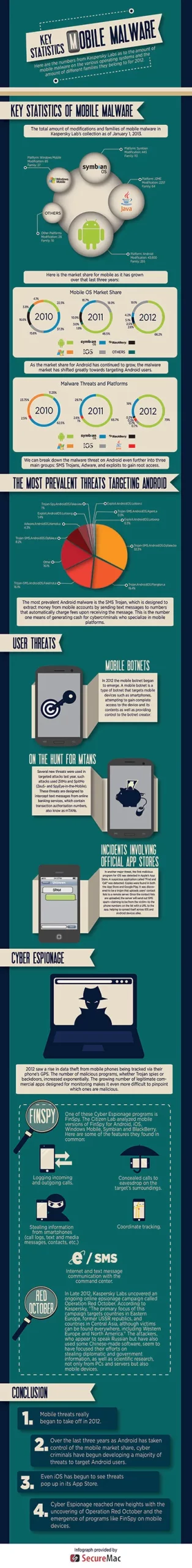
SecurityWe created an infographic to help show an assortment of statistics highlighting the changes in both mobile OS popularity and the malware that associated with each over the past three years.
May 20, 2013 •
1 min read
SecuritySecureMac announces the release of PrivacyScan 1.2, a specialized app to seek and destroy privacy threats for the Mac, now available in the Mac App Store. PrivacyScan is a utility designed for people who value privacy and want to keep their online and offline experiences…
March 26, 2013 •
1 min read
Security5 Easy Tips to Keep Your Mac Secure in 2013 has been published and is now available for immediate implementation to help keep you secure this New Year! Which methods are you already using and how do you rank?
January 8, 2013 •
3 min read
SecuritySecurity researcher Israel Torres for SecureMac has published his latest piece about OS X security entitled 10 Security Tips for Safe Computing for OS X Mountain Lion. The in-depth article covers many aspects of OS X’s built-in security features and how to use them to your benefit.
November 28, 2012 •
5 min read
SecurityAugust 10, 2012 – Las Vegas, Nevada – SecureMac releases MacScan 2.9.4 offering full Apple Mac OS X Mountain Lion (10.8) support as well as interface updates and enhanced support for both Firefox and SeaMonkey web browsers. The latest version also adds the latest definitions…
August 10, 2012 •
2 min read
SecurityMac OS X 10.7.3 (Lion) inherently contains many desired security features; however it takes a few moments for the user to enable most of them. It’s the ideology of convenience versus security and as it is well known Macs are quite convenient. This article will…
May 12, 2012 •
10 min read
SecurityPrivacyScan 1.1, Privacy Protection for Your Mac, is now available in the Mac App Store with new and improved privacy cleaning features. PrivacyScan protects online and offline privacy by shredding files that can be used to track your web browsing and computer usage. PrivacyScan’s shred functionality is able to overwrite sensitive data up to 35 passes!
April 11, 2012 •
3 min read
SecurityFrom Doctor Web, the Russian anti-virus vendor—”conducted a research to determine the scale of spreading of Trojan BackDoor.Flashback that infects computers running Mac OS X. Now BackDoor.Flashback botnet encompasses more than 550 000 infected machines, most of which are located in the United States and Canada. This once again refutes claims by some experts that there are no cyber-threats to Mac OS X.”
April 4, 2012 •
1 min read
SecuritySecureMac has learned of a new piece of Mac malware that is currently in the wild and infecting computers running OS X. As first reported at http://labs.alienvault.com/labs/index.php/2012/alienvault-research-used-as-lure-in-targeted-attacks/ this piece of malware exploits a vulnerability in computers running older, unpatched versions of Java.
March 20, 2012 •
2 min read