SecurityWhile the average user might think their operating system options only go so far as “PC or Mac”, the truth is that there are many more systems running behind the scenes which power a great deal of our digital infrastructure. Linux is one such system,…
February 14, 2019 •
3 min read
SecurityOn this week’s episode we talk about: apps that record what you’re up to, pirates on the Enterprise, and 2FA has a day in court (for some reason).
February 14, 2019 •
11 min read
SecurityThis week, a return to form — at least in terms of format. We’ve got follow-ups on stories from previous weeks for you, but we’re also hitting some big stories in security news this week. That includes another major event concerning Apple security and the…
February 7, 2019 •
12 min read
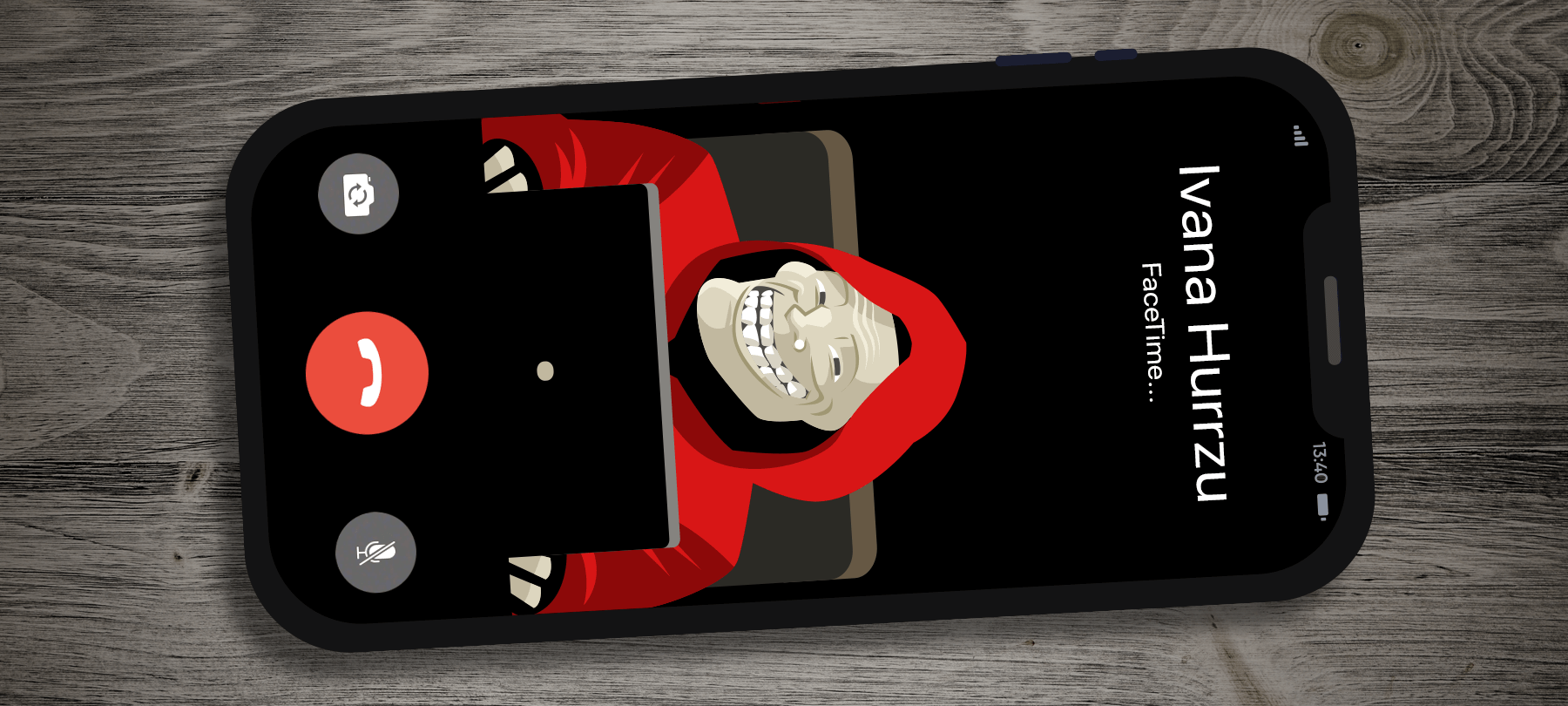
SecurityWhen Apple debuted iOS 12.1 late last year, one of the flagship additions to the system was Group FaceTime. This long-requested feature allows multiple users to enjoy simultaneous face-to-face video chat through FaceTime. However, in the wake of a serious flaw in Group FaceTime that…
February 6, 2019 •
3 min read
SecurityIt’s here: the first array of security updates in the new year for everything from macOS to iOS. These updates don’t roll out any brand new bells and whistles or slick new features, but they do address a host of flaws that require a fix….
January 31, 2019 •
2 min read
SecurityOne story today… with lots of little stories nestled inside… Longtime Listener, FaceTime Caller… time to hit the Checklist.
January 31, 2019 •
11 min read
SecurityJan 24, 2019 It’s the end of the world as we know it — or at least, for one Californian family, that’s what it seemed like for about thirty minutes or so. Meanwhile, the police are leaking data all over the place online, but hey,…
January 24, 2019 •
9 min read
SecurityWith January slipping by quickly, are you back in the groove of all your usual life responsibilities? Are you perhaps enjoying your free time by taking advantage of all those new gadgets you got over Christmas, such as a brand-new TV? It may have some…
January 18, 2019 •
12 min read
SecurityThe year may not yet even be a few weeks old, but already the headlines have been crowded with a range of issues that Apple users would do well to notice. From malware slipping past Gatekeeper to a mysteriously cancelled hacker conference appearance, there’s plenty…
January 14, 2019 •
3 min read
SecurityIt’s a new year — but some old worries have followed us into 2019, still lingering and causing some concerns. That means it’s time to shake off the last of the sleepiness still hanging around from the holidays and get back down to business. We…
January 11, 2019 •
11 min read
SecurityThe holidays are here — and so is the entire Checklist crew! On this week’s special holiday edition of the show, we’re veering into something new and fun. Rather than bringing you depressing stories about data breaches or the headlines about whatever Facebook’s latest follies…
December 20, 2018 •
10 min read
SecurityApple recently released a comprehensive set of security updates, affecting devices and applications ranging from the iPhone to the Apple Watch to iTunes to the Apple TV. Below, we have outlined some basic details about these updates, including the devices they are intended for and…
December 17, 2018 •
3 min read
SecurityWith the New Year starting to peek over the horizon, The Checklist is heading to Oz in this week’s discussion — not in terms of “The Wizard of,” though, but “Australia!” There’s a story from Australia this week that has us quite cross, though we…
December 13, 2018 •
9 min read
SecurityLas Vegas, Nevada — With more than 118 episodes in the history books, SecureMac is proud to mark the passing of two years since the initial launch of The Checklist, a weekly privacy and security-focused podcast for users of iOS, macOS, and all things Apple….
December 11, 2018 •
3 min read
SecurityAs we get back into the groove of things in between the major holidays, the security hits keep on coming as it starts to look like there are more than just a few weeds in the “walled garden” that is the iOS App Store. Elsewhere,…
December 6, 2018 •
12 min read