
Highlights from Verizon’s 2022 Data Breach Investigation Report
Verizon’s data breach report annual report is a good way to see how the data breach landscape is changing.
May 31, 2022 • 5 min read
Verizon’s data breach report annual report is a good way to see how the data breach landscape is changing.
May 31, 2022 • 5 min read
The GM data breach; are e-learning platforms spying on our kids; Apple boosts user privacy with new “easy delete” rule.
May 26, 2022 • 4 min read
Checking an AirTag’s battery life and firmware version, Apple’s latest updates, two ads on privacy from DuckDuckGo and Apple.
May 19, 2022 • 4 min read
What to do after you turn parental controls off on your child’s Apple device. 4 conversations you need to have with your child.
May 18, 2022 • 5 min read
FIDO standards for passwordless login: Is this the end of passwords? An interview with Megan Shamas of the FIDO Alliance.
May 13, 2022 • 6 min read
It’s World Password Day 2022, and we’re talking password security. We’ll cover common password mistakes + a list of best practices to follow!
May 6, 2022 • 5 min read
The problem with fake electronic data requests; plus, IoT security tips as attacks on smart devices rise to nearly 1 billion per year.
April 28, 2022 • 6 min read
The 2022 Mailchimp breach: What happened, impact on Trezor customers, and cybersecurity takeaways for everyday users.
April 25, 2022 • 6 min read
Best of The Checklist: Google finds more 0-days; NSO Group spyware is back; and educating future cybersecurity pros!
April 21, 2022 • 2 min read
We’ll talk about sideloading on iOS and how it might impact user privacy. Plus: Why AirTag stalking may be a more serious problem than everyone thought.
April 16, 2022 • 5 min read
Cybercriminals are using fraudulent Emergency Data Requests (EDRs) to convince tech companies to give them sensitive user data. Read on for more information about the problem and some tips to help you stay safe.
April 14, 2022 • 11 min read
The US acts on cybersecurity. The FBI disables a Russian botnet called Cyclops Blink, and a new cybersecurity bureau is born.
April 12, 2022 • 3 min read
A phishing awareness refresher. Mysterious texts that come from your own number. The 2021 FBI Internet Crime Report.
April 8, 2022 • 5 min read
What to do about a lost iPhone: Apple makes it harder to repair iPhones marked “missing”; lost iPhone tips and tricks; turning on Find My.
April 1, 2022 • 6 min read
Bad actors abuse TestFlight and WebClips to scam iOS users. Lessons in why you shouldn’t install apps from outside of the App Store.
March 25, 2022 • 5 min read
In all, Apple issues 159 security fixed in this round of updates.
March 19, 2022 • 4 min read
Cyberattacks in the Russia–Ukraine war. Discusses attacks before the war, ongoing cyberattacks, Ukraine’s cyberdefenses, and more.
March 16, 2022 • 5 min read
March 2022 Apple updates for macOS, iOS, iPadOS, watchOS, tvOS, and Apple software. Covers security highlights and discussion of impact.
March 15, 2022 • 4 min read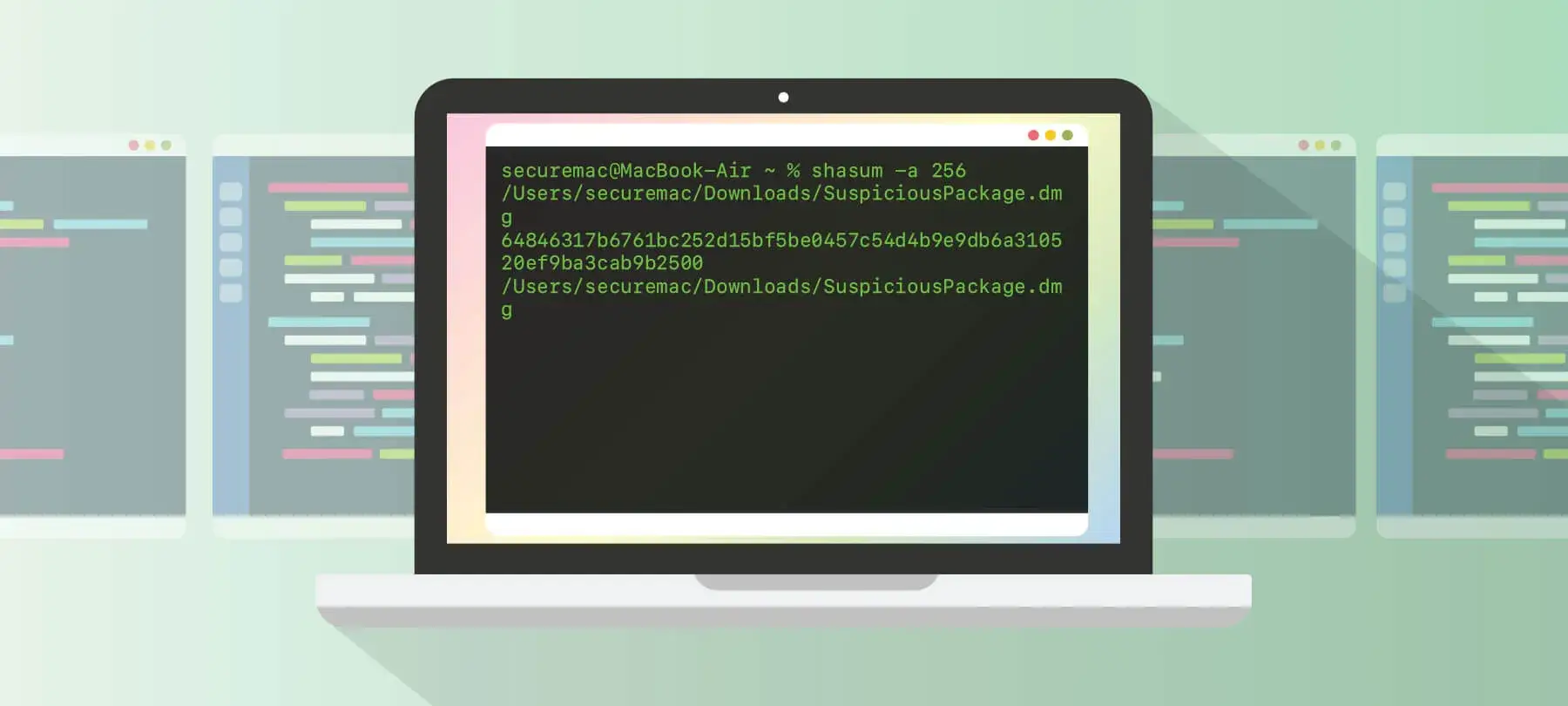
How to use checksum on Mac to verify downloads. This guide gives you the steps needed to verify a checksum in Terminal.
March 15, 2022 • 10 min read
SecureMac’s guide to Mac Trojan horse malware, updated and expanded for 2022. Covers definition, capabilities, variants, and how to avoid.
March 14, 2022 • 10 min read