Mac OS X Security Issue: FileVault Leaves Unencrypted Data Behind
Mac OS X FileVault Security Advisory
Advisory Title: FileVault Leaves Unencrypted Home Data Behind
Release Date: 2003 November 6
Fix Date: Mac OS X 10.4 (May 2005)
Affected Product: Mac OS X 10.3 Build 7B85
Impact: Unencrypted Data Left Behind
Where: Local System
Author: CodeSamurai (codesamurai@mac.com)
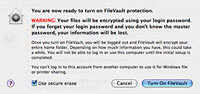 Update (Mac OS X 10.4): With the release of Mac OS X 10.4 (Tiger), Apple has included a fix for this in the FileVault enabling process. When the user goes to enable FileVault on their user account in System Preferences, one of the sheets will now have a “Use secure erase” checkbox. Have this checkbox checked in order to avoid the issue described in this advisory. Note: that this issue is not resolved in 10.3.
Update (Mac OS X 10.4): With the release of Mac OS X 10.4 (Tiger), Apple has included a fix for this in the FileVault enabling process. When the user goes to enable FileVault on their user account in System Preferences, one of the sheets will now have a “Use secure erase” checkbox. Have this checkbox checked in order to avoid the issue described in this advisory. Note: that this issue is not resolved in 10.3.
Overview
It is possible to recover the remnant data of a home folder which to which FileVault has been enabled. In other words, FileVault doesn’t clean up after itself (securely).
Details
Most would assume, that by enabling FileVault on their home folder, that it “protects all the info in your home folder from prying eyes”[1] as stated on Apple’s web site. And granted, this is true of the data which is in FileVault; however, the security in regards to the process of enabling FileVault on an existing home folder leaves a little to be desired, as the data before FileVault is enabled is insecurity left behind in the hard drive’s free space.
FileVault itself is an AES-128 encrypted disk image, and when it’s enabled on a home folder, that home folder’s contents are copied to the disk image and securely stored there; but when the original home folder is erased, it is done so without doing a secure erasure. This means that file recovery programs will be able to recover some, if not most, of that user’s home directory data in the condition it was before the transfer to FileVault. So, the data is left behind, unencrypted, with the user under the impression that that data is now only located in secure containment of FileVault.
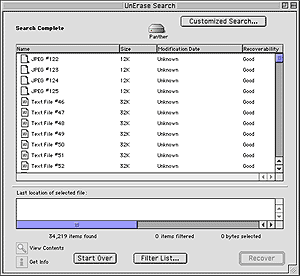
Recommendations
To resolve this, one could use a program to securely wipe the free space of their hard disk; or, if they’re doing a fresh install of Panther, to copy their backups back over to their hard drive after FileVault has been enabled. (The latter of which is stated under the assumption that the user is installing Panther on a new hard drive or that the drive has already been written over with zeros via Apple’s Disk Utility or securely erased otherwise; because, for obvious reasons, the data of the previous installation will be still left behind in the hard drive’s free space anyway.)
