20+ Top Security Tips for Safe Computing Mac OS X – Mac OS X Trojan Horse
Mac OS X 10.7.3 (Lion) inherently contains many desired security features; however it takes a few moments for the user to enable most of them. It’s the ideology of convenience versus security and as it is well known Macs are quite convenient. This article will discuss how to further harden the Mac OS X environment and raise users up a few notches from the low-hanging fruit category.
General Security
Built-in – Using the operating system’s native toolset available for the user to configure and raise the security posture from its default ‘convenient’ settings. For example System Preferences, Keychain Access, Software Updates.
Third-Party – Using third-party vendors to further enhance the native system usually with additional front-ends. For example 1Password, Little Snitch.
Encryption Security
Built-in – Using native available encryption. Apple comes with FileVault 2; a whole disk encryption feature allowing users to have their data made irrecoverable in an event of theft, loss, physical compromise.
Third-Party – Using both open source and/or commercial encryption suites such as TrueCrypt, Mac GPG, Symantec’s PGP Desktop.
Malware Security
Built-in – Using native available malware protection. XProtectUpdater which updates the ‘safe downloads list’.
Third-Party – Using both commercial and/or free anti-virus/anti-malware suites such as MacScan, Sophos, ClamXAV.
For the most part by configuring and enabling the built-in security features that Apple Mac OS X Lion has to offer third-party utilities turn into a ‘want’ more than a ‘need’.
Post-Installation
Security begins at… well the beginning. For most users this is known as post-installation. Just around where they would turn on their Macs for the very first time. The following 21 recommended security tips are not only recommended but also encouraged:
1. Create Your Computer Account
During this screen enter a password make sure the checkbox labeled ‘Require password when logging in’ is checked. If a password hint is entered make sure it doesn’t reveal to a potential attacker the password. I like to put in an appropriate message directly to the attacker such as ‘Sorry buddy, it isn’t that easy – try something else’. Note that Apple states “Enter a hint to help you remember your password. Anyone can see the hint, so choose a hint that won’t make it easy to guess your password.”

2. System Preferences : Change Lock Security Feature
Locking system preferences configurations is ideal in a secure world as to make changes requires authentication with administrative credentials. Of the 29 default System Preferences 11 locking options are offered by default in Security & Privacy, Energy Saver, Print & Scan, Network, Sharing, Users & Groups, Parental Controls, Date & Time, Software Update, Time Machine, Startup Disk. The padlock icon is on the lower left and does not take a password to enable; but takes a password to disable.

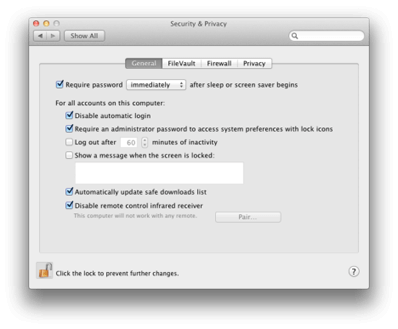
3. System Preferences:Security & Privacy:General
The following recommendations are obvious, but only a few are enabled by default verify the following are enabled.
Require password immediately after sleep or screen saver begins.
For all accounts on this computer:
- Disable automatic login
- Require an administrator password to access system preferences with lock icons
- Automatically update safe downloads list’
- Disable remote control infrared receiver. “This computer will not work with any remote” otherwise if a remote is used make sure it is paired ahead of time. (If it is left unchecked or unpaired any Apple remote will be able to control the Mac by default)
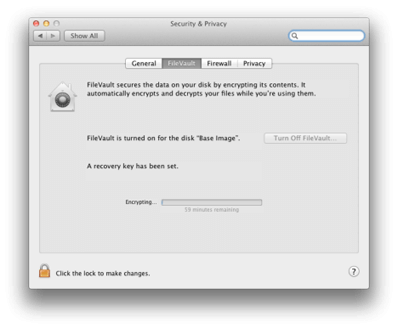
4. System Preferences:Security & Privacy:FileVault
Turn On Filevault
- Save the recovery key (text or screenshot)
- Enable Do not store the recovery key with Apple
- Restart the Mac to begin the encryption process
- Upon restart the background will now be gray and feel slightly different (reminding the user FileVault 2 is being used)
- Returning to System Preferences on FileVault it will display the time remaining for encryption process to complete (depending on the hard disk size and contents the time to completion may vary – it is recommended to let this run overnight without disturbance).
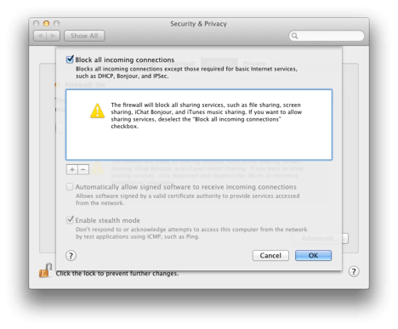
5. System Preferences:Security & Privacy:Firewall
Start the firewall (by default it is disabled)
It is recommended to configuring the firewall in the following order:
- Enable Stealth Mode
- Disable Automatically allow signed software to receive incoming connections
- Block all incoming connections
Note this will allow the Mac to use the network ‘normally’ however will not allow potential attackers to detect or attack the Mac easily when compared if these features were left disabled.
6. System Preferences:Security & Privacy:Privacy
Naturally these settings are for the truly paranoid and in trade will not automatically allow applications or Apple have an understanding on the issues or whereabouts of the Mac.
- Disable Location Services
- Disable Send diagnostics & usage data to Apple
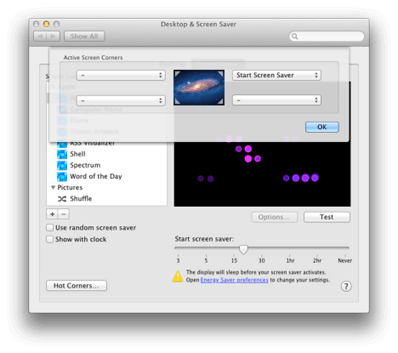
7. System Preferences:Desktop & Screen Saver:Screen Saver
When not at the keyboard the screen should be lock. This is good practice for the security conscious. A simple method to lock the screen is to enable a hot corner where the mouse can be positioned to activate the screensaver in essence locking the screen.
Choose a Screen Saver and Choose Hot Corners and select an Active Screen Corner
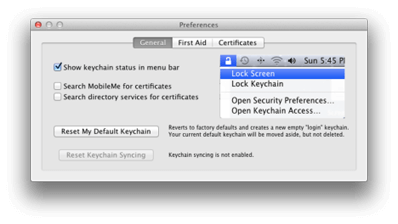
Note: Another way to lock the screen using the mouse would be to open the Keychain Access app Preferences and enable Show keychain status in menu bar. This adds the Lock Screen feature and a padlock icon in the menu bar for easy access to lock the screen with the click of the mouse.
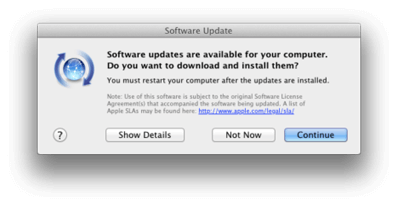
8. Software Update
Now that the system is secured on the network Software Update is the next logical feature to run so that the Mac acquires the necessary security updates to the machine.
Note: Prior to doing this it is recommend waiting for FileVault to complete the encryption process before downloading the updates (off the network). FileVault is known to be sensitive to disk activity during the encryption phase.
For the updates themselves It is always recommended to Show Details and review the items prompting to be installed; for the most part the user is safe but it can never be assumed. Install the new software available for the Mac. If it is necessary to choose priority due to bandwidth limitations select the Mac OS X Update Combined first as that has most of what is needed first. Note: If Software Updates downloads are giving issues they can be downloaded as dmg files from Apple’s support site: http://support.apple.com/downloads/
Remember to run Software Update a few times to make sure that everything is updated. Sometimes after updates are downloaded and installed after restarting there are a few more. It is best practice to check and make sure to get the message “Your software is up to date”.
9. System Preferences:Bluetooth
If Bluetooth isn’t being used disable it by clearing the checkbox labeled On. If it needs to be used for the magic mouse or other bluetooth device and and doesn’t require it to be set as Discoverable then also clear the checkbox labeled Discoverable; thus lessening potential attack vectors.
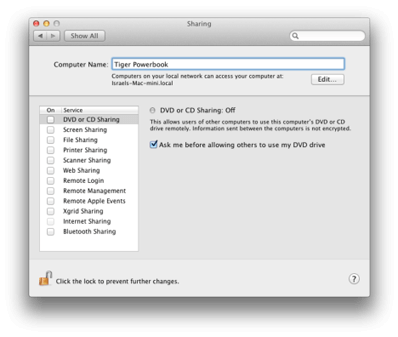
10. System Preferences:Sharing
Change the Mac’s name – for best results give it a name that doesn’t stand out to potential attackers by revealing a tasty target. Apple by default will give the computer name as the first user’s first name and then the type of computer – i.e. ‘Israel’s Mac Mini’. For example to seem really uninteresting a name such as ‘Tiger Powerbook’ may discounted by an attacker as a crusty box be passed on for newer technologies.
11. System Preferences:Users & Groups
Make sure to only allow user to administer the computer if it makes sense; don’t just do it by default – add parental controls if need be; however Apple’s Parental Controls are simple and rather limited; most savvy individuals can bypass these tools.
While here verify that all services are disabled by default, and be careful to enable anything – be sure to understand what type of risks it puts the Mac and ultimately the end-user in.
12. System Preferences:Date & Time
It may not seem like a big deal but the Mac is a precision machine that relies on date and time to make sure things are happening that are supposed to be happening. If there are new issues the first thing that should be checked is the date and time. Especially if it is password related; some systems won’t tolerate an environment if it is more than 5 minutes off. By default Macs are synched to the apple time server time.apple.com. (as long as DNS hasn’t be compromised along the way this should suffice)
13. System Preferences:Software Update
Verify that Check for updates weekly and download updates automatically are enabled. For the most part updates (especially security related) should be gotten and applied sooner than later.
14. System Preferences: Spotlight: Privacy
Some things don’t need to be indexed and therefore should remain private. Not only does not indexing them speed the performance of spotlight. It also adds security by not storing the location of certain data. To do so indicate and add which locations shouldn’t be searched.
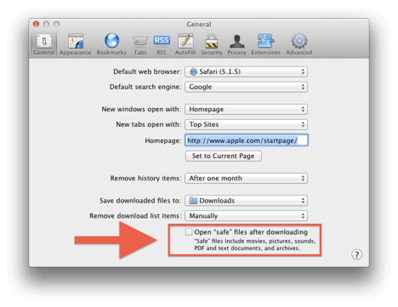
15. Applications:Safari: Preferences: General
In Safari’s General Preferences disable ‘Open “safe” files after downloading. What Safari may think as safe; may not be. They will be downloaded to the Downloads folder where the user can open then and extract them as needed.
16. Applications:Safari: Preferences: Autofill
Verify User names and passwords is set to disabled. Don’t use this if the ramifications aren’t clear.
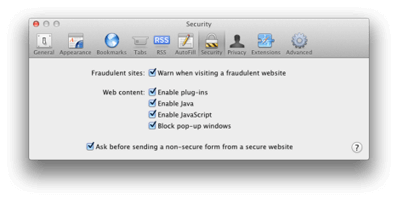
17. Applications:Safari: Preferences: Security
By default all items are enabled; be sure to gloss over time and verify that’s what is needed. Disabling one or more of these may alter the user’s browsing experience.
18. Applications:Safari: Preferences: Privacy
Privacy is another pre-populated configuration that doesn’t require manipulation unless it is necessary.
19. Applications:Safari: Preferences: Extensions
Extensions should be off unless extensions are being explicitly used. (available from extensions.apple.com)
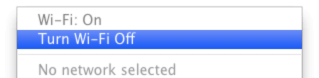
20. Menubar: Wi-Fi
If Wireless connectivity is not being used it should be turned off to eliminate accidental connections and exposure to untrusted networks.
21. Post-boot
Unbeknownst to most Mac users Apple computers have a fantastic built-in feature that allows the physical machine to be locked down (with a password) from further tampering and/or unauthorized examination. For example booting up to optical media or alternate disk thus bypassing the built-in authentication mechanisms to gain access to the unencrypted contents of the hard disk ala the ‘Evil Maid Attack’. To enable this feature boot to the Lion recovery partition (during startup hold the Command+R keys on Lion 10.7.3) and in the Mac OS X Utilities menu navigate to Utilities-> Firmware Password Utility to Turn On Firmware Password. [Note: do not forget this password as it will be quite difficult to gain access back into the machine through normal means, and may require consultation with the Apple Genius at added expenditure]
Securification
For additional configurations and actions about Apple Mac Security peruse through Apple’s security guides http://www.apple.com/support/security/guides/
Users unaware of all the fantastic tool Mac OS X Lion comes with to further protect their data and privacy should be encouraged to consider setting a few if not all the aforementioned built-in security features. Doing so only takes a few moments of time. Hopefully in the future Apple will attempt to suggest enabling these security features automatically (and conveniently) during post-installation especially for new users via a simple security wizard. One key facet to security is preparation and to quote Benjamin Franklin: “By failing to prepare you are preparing to fail.”
Online Resources Mentioned Herein:
1Password: https://agilebits.com/onepassword
Little Snitch: http://www.obdev.at/products/littlesnitch
TrueCrypt: http://www.truecrypt.org/
Mac GPG: http://macgpg.sourceforge.net/
PGP Desktop for Mac: http://www.symantec.com/
MacScan: http://macscan.securemac.com/
Sophos: http://www.sophos.com/freemacav
ClamXAV: http://www.clamxav.com/
