10 Security Tips for Safe Computing for Mac OS X and MoutainLion 10.8
OS X, formerly named ‘Mac OS X’, is ever increasing its integral and nearly transparent security configuration on each progressive release. As of this writing we are at Mountain Lion 10.8.2 and will go over the latest and greatest security updates.
If you haven’t already please review the previous article ‘20+ Top Security Tips for Safe Computing for Mac OS X‘ for additional security tips that still remain relevant today.
The following 10 security tips take advantage of the latest Mountain Lion security features:
1. Gatekeeper
Gatekeeper’s control resides under Preferences/Security & Privacy and it’s main function is to allow the user to control which apps can be run without further escalation and or attention. For example it is by default to ‘Mac App Store and identified developers’ so if you download an application that doesn’t meet this criteria you will not be able to run the application immediately or more so accidentally.
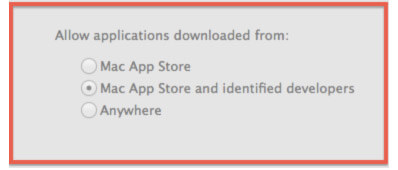
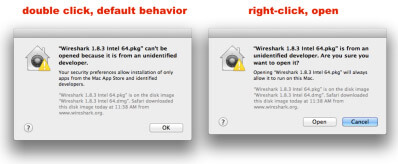
You can either change the preference to ‘Anywhere’ (not recommended) or simply right click (or control click) on the App instead of the normal single double click to open it.
2. Software Updates
Updates often gets overlooked as a security measure; however fundamentally you want to keep your Mac updated with the latest and greatest updates. Most often users don’t update their Macs to the latest because the update has phased out their application from working, or the user feels they are too busy to update their Macs. Don’t be that user. Instead inquire with the software developer’s support system to find out what they are doing about their incompatible product – many often become aware of this issue through their internal testing and generally try to push out a patch or updated version quickly. If they lag see if you can find an alternate product until they update. It’s always good to have another good product on standby.

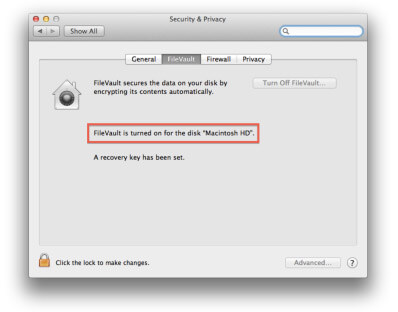
3. FileVault 2
Laptop and even Desktop encryption should be automatic nowadays. Losing a few thousand dollars of hardware is much better than losing all your data to someone later to find it pasted all over the Internet or worse sold on the blackmarket. Use whole disk encryption any chance you get. The rewards far outweigh the risks.
FileVault 2
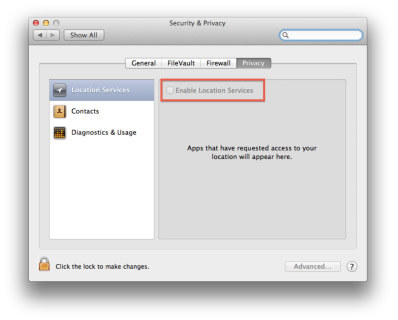
4. Privacy Controls
Privacy is important and shouldn’t be taken for granted. Make sure you keep track of whom is keeping track of you by tuning your privacy controls accordingly.
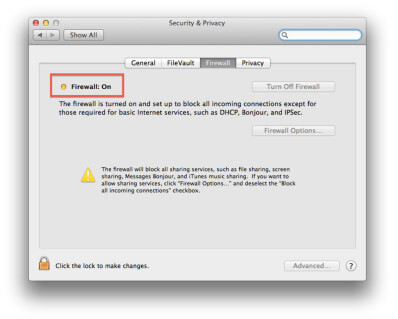
5. Firewall
The firewall interface under Preferences/Security & Privacy is very basic, there are a few third party interfaces available however keeping things simple is a good practice. Be sure to use the firewall to tune it to your needs whether it be at home, work or travel. You may think you have nothing to hide, however you have plenty to steal.
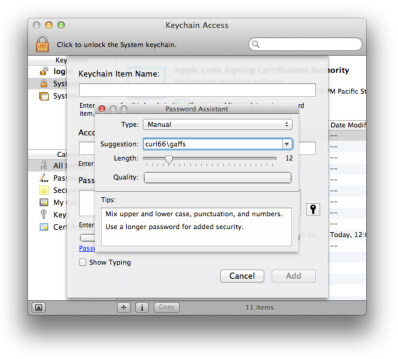
6. Password Assistant
Face it, for most creating a good password is hard. It involves a lot of thinking not only to come up with one that you don’t already use, but then remembering it without having to write it down is a task within itself. This is where Keychain Access is your friend, use it. Inside Keychain Access is a handy tool named Password Assistant you can use it to quickly come up with a password and you can save it in your keychain to use on various logins.
7. Anti-phishing
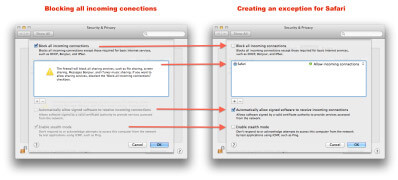
For those that use Safari (6.0.2 ) over Chrome or Firefox you may have to make a firewall adjustment otherwise Safari may not be able to communicate correctly to receive updates from the The Google Safe Browsing Service, therefore leaving your browser out of date and more vulnerable.
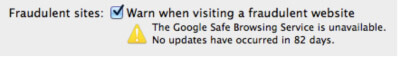
Below are the recommended firewall modifications for this:
8. iCloud Mac locator and remote wipe
For those that use iCloud your Mac can be enabled similar functionality as your iDevices for communicating with your Mac if it gets lost or stolen once it is reconnected to a network. It certainly is better than nothing, however you have less to worry about if you use FileVault2 to encrypt your Mac.
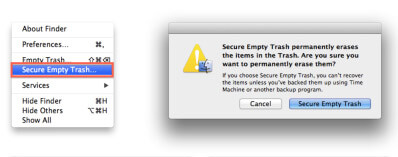
9. Secure Empty Trash
Another feature the Mac users may forget to use often especially on USB keys is the Secure Empty Trash Feature. By default files are simply marked for deletion and not really deleted making file recovery simple for an attacker. Using Secure Empty Trash things get much more difficult to recover.
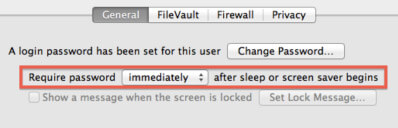
10. Control Access
Make sure you are the only person accessing your account by requiring a password immediately after sleep or screen saver begins. Enable a hot corner to activate the screensaver and get used to hitting that hot corner before leaving your Mac. Get used to doing this at home and it will come naturally everywhere else.
In conclusion…
Mountain Lion comes with a plethora of integral security features not really meant for the user to control such as file screening, sandboxing and runtime memory protection and without an interface to monitor or view users don’t think about it and just trust it. However as you could see in the Anti-Phishing example above with Safari unable to update for the last 82 days it becomes curious as to what else may not be working as designed. 😉
Online Resources Mentioned Herein:
http://www.apple.com/osx/what-is/security.html
http://support.apple.com/kb/HT5501
http://www.apple.com/support/security/guides/
http://www.apple.com/support/icloud/find-my-device/