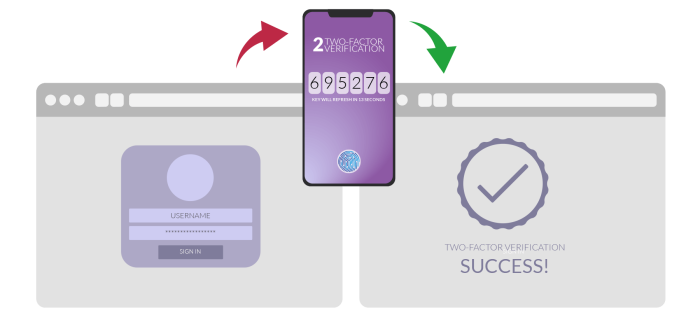
SecurityTwo-factor authentication, or 2FA, is one of the best cybersecurity tools available to you. The main benefit of two-factor authentication is that it adds another layer of protection to your accounts and services, above and beyond passwords
January 8, 2020 •
11 min read
SecurityAndroid has started rolling out Rich Communication Services (RCS) chat features to users of its Messages app, touting this as a better, more up-to-date successor to traditional SMS texting. However, there is still some confusion about what RCS is…
January 7, 2020 •
6 min read
SecurityMany people are aware that large tech companies like Facebook and Google collect and monetize user data . But privacy advocates are now sounding the alarm about the growing trend of consumer banks and credit card companies doing the same thing.
January 6, 2020 •
8 min read
SecurityThis January, we’re going to offer you the chance to make some changes which will improve your cybersecurity posture and keep you safer all year long. To do this, we’ll give you some background information on each “cybersecurity New Year’s resolution” and also walk you…
January 2, 2020 •
8 min read
SecurityThe Checklist is taking a little holiday break this week, but we’ll be back on the 9th of January with a new podcast. Until then, we’d like to invite you to check out these classic Checklists you might have missed, especially as they touch on…
January 2, 2020 •
5 min read
SecurityThis year was a big one for cybersecurity news, with plenty of stories worthy of inclusion in a year-end review. We’ll take you through the top stories of 2019 which help us see the shape of things to come.
December 27, 2019 •
8 min read
SecurityIt’s that time of year again, when kids and adults alike will soon be unwrapping presents and playing with new toys. But if you receive an Internet of Things (IoT) device as a gift, you may want to pay extra attention to the cybersecurity ramifications…
December 22, 2019 •
6 min read
SecurityIt’s that time of year again, when Santa makes his list, checks it twice and, well, you know the rest. So in the spirit of the season, we’re going to take a look at some of the top Apple stories of 2019 to see if…
December 20, 2019 •
9 min read
SecurityThis week’s Checklist topics may sound familiar, but don’t be fooled! We revisit three stories that we’ve talked about before, but which now have some updates worth discussing (spoiler: it’s not all good news!). On this week’s Checklist, it’s deja vu all over again: $20…
December 19, 2019 •
11 min read
InterviewsGeorgia Weidman is a penetration tester, security researcher, writer, trainer, and entrepreneur. She is the author of a highly-regarded book which teaches the fundamentals of penetration testing, Penetration Testing: A Hands-On Introduction to Hacking, and has taught security courses and conducted advanced training sessions at…
December 17, 2019 •
13 min read
SecureMac Company Press ReleasesCybersecurity firm has changed with threat landscape; looks to future
December 17, 2019 •
3 min read
SecurityCupertino rolled out new features and bug fixes for all of its operating systems, so we’re going to take a look at last week’s security news broken down by OS.
December 12, 2019 •
8 min read