GrouchySmurf 1.0 – Spoofed Broadcast ICMP
GrouchySmurf is the first public release of an ICMP broadcast attack for the MacOS. Last night the application was released by Freaks Macintosh Archives a hacker related website for the macintosh community. They wrote a review/press release on the application to hype it. Now it is online and available for download. The ICMP broadcast attack will be explained in details further in this document.
Were not going to try to hide the bad uses of this program. This review is to inform you of the new software released and what damages it might cause. This is not a new attack or exploit, just the first time ported to the MacOS. This software can be used for good uses (personal testing of your own servers vulnerabilities, etc) or bad uses (flooding someone off the net, causing bsod’s (blue screen of death), crashing the machine, slowing down servers, etc).
What’s a broadcast / Quick ICMP broadcast attack
First of all, lets put something clear: a broadcast is _not_ a machine, it is in fact the address of a whole subnet of machines. Machines over the internet have IP addresses in the form x.x.x.x where each x is a number between 0 and 255 (of course alot of those addresses are special addresses and not all of them are used as standard IP addresses, but you already knew all that..) So here is what interests us, lets say we have a LAN (Local Area Network) which IP addresses belong to the subnet 205.151.222.x. The default gateway address would be 205.151.222.1, and the subnet’s actual address would be 205.151.222.0. The broadcast address would be 205.151.222.255.
Here’s what interests us, the broadcasts and subnet addresses, which do pretty much the same thing in that case. Now lets say a machine on our LAN wants to send a packet that everyone will read, this is called a broadcasted packet, the machine will send it to 205.151.222.255 or 205.151.222.0 (255 is the most commonly used though.). The machine actually sent one packet which was read by ALL the machines on this subnet. Now lets say that machine sends a PING to the broadcast address, what will happend? well all the machines on the subnet will reply to this machine with an ICMP echo reply.
Now this should _only_ work with local area networks, this means the gateways should only broadcast packets coming from the INSIDE of the network. The reason I say should though is that there is obviously an exception, and a big one. Alot of gateways over the internet are misconfigured and allow broadcast packets to come from the outside. This means if I send a PING to the subnet’s broacast, each machine will reply with one ping, amplifying my PING by the number of machines on this subnet.
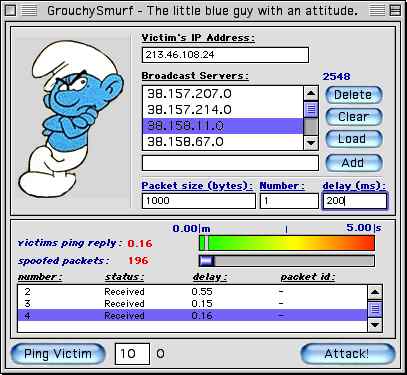
The ICMP broadcast attack uses a list of those vulnerable broadcast servers and send PING to those broadcast servers, those packet’s source address is spoofed to the victim’s IP address, so all the ICMP echo replies are sent back to the victim, and not to you, the real source.
Download
Freaks Macintosh Archives Download
Fix
This vulnerability is very easy to fix, it fact it resides in telling your router not to broadcast packets coming from the exterior (the internet in this case), therefore only broadcasting local packets. You can import directly a list of your own servers which might be vulnerable or enter them manually (and save it to test them again, if you wish, when measures are taken.). The best way to know which servers responds would be to use an ICMP logger and attack your own machine. The built-in ping utility allows you to test lag on a remote machine and has various uses, such as making sure you do not blow off the net the machine you are using for monitoring purposes.
