Security Auditing Tools for the Macintosh
Security Auditing Tools for the Macintosh
In today’s media you only hear about hackers rummaging through data stealing important information. You hear about how your security becomes more and more insecure. All these hackers are hitting websites, stealing passwords and credit card numbers. Yes, it’s true a lot of this doesn’t pertain to the MacOS. It’s the Windows and UNIX servers being hacked. Yet it does happen. Administrators don’t take the right precautions to ensure their customers are secure. The customer is thought to be dumb. It is believed that not all people know enough to have a secure password, (i.e., one with more than 4 characters and containing numbers).
There really aren’t any ‘security’ tools for the Macintosh to ensure secure passwords. Just lots of text files and reports by hackers on how it’s insecure. We will review two programs created by hackers, which can be used for security purposes, and can be used by a hacker. The reason we are reviewing these hackers programs is to bring to light that you need to know the tools that hackers are using to ensure your own security. Get the programs before the wrong people do and use them on your unsuspecting computers. We will review these programs from a system administrators’ point of view.
MagicKey (known as ‘MK’) is an application made by the programmer, ‘System Cowboy.’ MK is a password-auditing tool for AppleTalk. The application audits the AppleTalk users file for weak passwords, the method it uses to discover these weaknesses is called �Brute Force
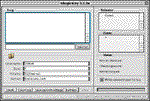
The program will attempt a combination of words and letters to try to match the encrypted data. If your mac is on a network sharing information, it is utilizing the AppleTalk protocol. If you use the mac to access the internet, malicious users could access it remotely using this program. Even on your own network you have to be ensured security. Start by ensuring secured passwords. If this application does pick up one of your users passwords, turn off their account until you talk to them and instruct a change of password.
MacPork, another popular program, quickly checks servers for known vulnerabilities and reports them.
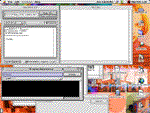
If the vulnerability results in a password file found, it will display it to prove the insecurity. There are many programs like this written for the UNIX platform to check servers. MacPork is the first complete application to do so for the MacOS. You can audit your whole network from this application, even your PC and UNIX machines. Once you identify a hole in your network, the next step is to fix it. To began with get the most recent version. If it’s already the most recent version, disable the function and contact the creator of the service to find out more information.
There are hundreds of other mac programs on the net that are used by hackers, but the administrators have not even taken a look at them. We are not warranting that hacker tools are all good, there are still the malicious ones out there. Be careful when experimenting and always run Anti-Virus software. The two programs listed above are guaranteed clean of viruses, so take a look and experiment with them when you have a chance. Feel free to bookmark this page along with all the other SecureMac.com pages because these resources will never become outdated.
