Mac OS X Firewalk – Firewall Configuration Utility
What is Firewalk?
Firewalk is a Mac OS X configuration utility for the built in firewall. While you are running Mac OS X you should be aware that you are running on a BSD/Mach kernal. The built in firewall that Mac OS X offers is rather dirty, some like to get into the unix part of the operating system others still prefer the nice Macintosh GUI. This application makes it possible for you to configure the firewall properly with the graphical user interface that Macintosh users are used to.
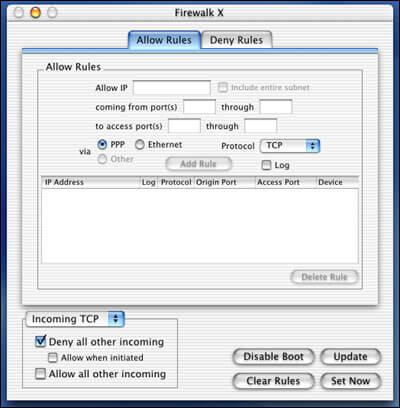
Firewalk X 2 offers all of the following in a single package
- Independent; does not rely on or use Mac OS X’s built-in firewall, ipfw
- TCP, UDP, and ICMP packet filtering, both incoming and outgoing
- Self optimizes to current network activity
- Interactive, real-time alerting
- Time expiring firewall rules
- Compatible with Mac OS X�s built-in firewall
- Can restrict network access to specific applications
- User and IP address specific application rules
- Detailed logging of events
- Automatic setting changes for different network locations
- Multithreaded for optimal performance
- Port scan and packet flood detection
- Nicely integrated with Mac OS X for transparent operation
- Full Unicode support
Information
Firewalk X 2 allows you to create TCP, UDP, and ICMP rules. Specify different source and destination ports, an incoming or outgoing connection, subnets, device, and more. You can also have location specific settings which will automatically change when the system’s network location is changed.
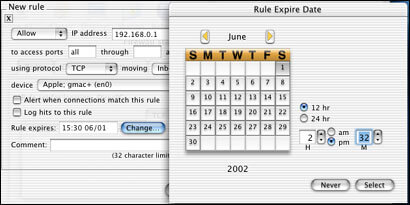
Being able to set specific rules to have expiration dates is a strong point of this program. Often users open up their whole network to allow a program or computer access to or outside the network and forget to change the settings back after they are done. With the expiring rules you can set it up so the rule expires in 13 hours, 2 hours, days, or weeks later so you do not forget and still maintain a secure network.
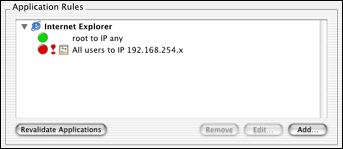
Network access can also be restricted to specific applications, your child shouldn’t be playing Diablo II online on your computer – only you can. Restrict it so Diablo II does not have network access until you want to play online.

