A pair of password stealing trojan horses from the App Store are wreaking havoc with Instagram accounts
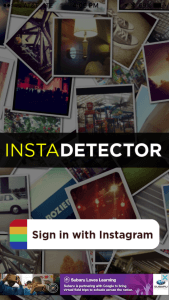
If you’ve recently downloaded InstaCare – Who cares with me? or the similarly-named Who Cares With Me – InstaDetector, you might want to double-check the security of your Instagram account.
The trojan horses, which were also being distributed in the Google Play Store, entice Instagram users with the lure of seeing who viewed their profile. Once installed, the malicious apps steal login credentials for Instagram, sending the username and password to a server controlled by malware author. From there, the affected Instagram accounts are hacked and used to post spam messages on the user’s feed.
Malware that makes it past Apple’s stringent review process and into the App Store is a rarity in and of itself, but a few key things make these new trojan horses even more notable:
Apple already knew about the malware author
The malware was listed in the App Store under the name Turker Bayram. An app released under the same publisher name was busted by Apple back in November 2015, when it was found to have pulled a similar stunt. At that time, the app was removed from the App Store, and that should have been the end of it. For reasons that aren’t readily apparent, Apple didn’t ban the malware developer’s account outright, which is the usual result in cases like this. Apple has the ability to revoke a developer’s code signing certificate, which is needed for an app to be able to run on an iPhone or iPad, and can quickly stop the spread of malware.
Not only did the author release new malware under the same publisher name, they created another developer account using Ismail Turkmen as the publisher name, which was then used to spread a second variant of the trojan horse. The new pair of trojans were spotted by eagle-eyed iOS developer David Layer-Reiss from Peppersoft, a small software development studio based in Germany. Layer-Reiss, who had an eye on the malware app publisher ever since discovering their first malware attempt last fall, has an in-depth analysis of the new threats on his site. Additional technical analysis can be found at the SecureList blog.
The trojans are still live in the App Store
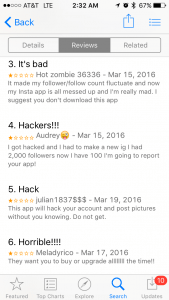
The fact that the malware has remained live in the App Store for an extended period of time, despite many users leaving 1-star reviews complaining about being hacked, is a bit strange. Normally Apple is very quick to remove malicious apps from the App Store, but these two trojans have been infecting a huge number of users for over six weeks. During this time period, the app has continued to rank high in the charts across the board, and is currently the #1 app in the entertainment category for Great Britain, and in the top 10 apps overall.
Prior to its removal from the Google Play Store, one of the trojans was listed as having between 100,000 and 500,000 installs, and it is likely that a large number of iOS users have been infected as well.
New language, new malware
The iOS variant of this malware was written in Apple’s new Swift programming language. Apps written in Swift, which Apple is touting as the future of app development for iOS, have been allowed in the App Store since September. While there are no technical hurdles when it comes to writing malware in Swift, this appears to be the first known example of Swift-based malware found in the wild. This shows that the bad guys are also keeping up with the latest technologies promoted by Apple.
So, you’re infected. Now what?
The first thing that users affected by this malware should do is change their Instagram passwords, using the “forgot password” link directly from the Instagram site if need be. Due to security restrictions put in place by Apple on iOS, it’s not possible for antivirus software to scan your iPhone or iPad directly. Instead, if you have the trojan horse on your iPhone or iPad, you will need to manually locate the InstaCare or InstaDetector app, tap and hold the app icon until it wiggles, then press the X button to remove it from your device.
If you sync your iOS device with your Mac, or if you have downloaded your iOS apps directly to your computer through iTunes, the malware may be present on your system. While this trojan horse cannot harm OS X itself, it’s a good idea to get rid of it so you don’t inadvertently sync it back to your iPhone or iPad. You can manually delete the trojan horses from your Mac by following these steps:
- 1. Open iTunes on your Mac.
- 2. Click the View menu at the top of the screen, click the More submenu, and then click Apps.
- 3. Locate the InstaCare – Who cares with me? or Who Cares With Me – InstaDetector app in the list, and single click the app to highlight it.
- 4. Either press the delete key on your keyboard, or select Delete from the Edit menu to remove the app from your system.
Users of MacScan 3 with up-to-date definitions can detect these trojans as iOS/Instealy.A and iOS/Instealy.B. MacScan will automatically check for malware definition updates every time you run a scan while connected to the internet.
Note: At the time this article was posted, the trojan horses were still live in the App Store, but had been removed from Google’s Play Store. This post will be updated as new details emerge.
Update (3/22/15 6:15 PM PST): Shortly after this article was published, SecureMac noted that one of the trojan horses had been removed from the App Store by Apple. The second trojan horse is currently still live in the App Store, and SecureMac has notified Apple.
Update (3/22/15 8:00 PM PST): At this time both variants of the trojan horse have been removed from the App Store.