Secure Installation of Mac OS X
This is one section of an overall document. The overall publication covers the setup of a Mac OS X Server. This part is being made public to help others secure their machines.
This document outlines some security measures for the Mac OS X Server 1.0 – 1.2 platform. While Mac OS X Server (OSXS) is a fairly secure environment out of the box, these basic measures help create a more secure computing environment. They should be taken by all personnel running a Mac OSXS on the WSU campus network.
The measures outlined here are based on a Mac OS X Server providing Mac services to a lab environment. These measures can be modified to work on other configurations. The goal is to provide an example of security measures that can be applied to a Mac OS X Server. While services may differ from server to server, the necessary service options apply to most configurations With time and practice, these options can be highly configured and can provide a good degree of protection. As with all security measures, however, one must be diligent to keep up with updates to applications, check logs, and be vigilant.
There are documents scattered throughout the web about BSD security: Mac OSXS is based on the Mach kernel and BSD UNIX. The most relevant information about Mac OSXS was gleaned from those documents and consolidated for the following pages.
ED: It is recommended that you revisit this page. As Mac OS X evolves, updates will be posted for Server and the new OS X.
All services listed here, were tested on a Macintosh G4 running Mac OS X Server 1.2. I have installed and configured the measures mentioned in this article. It is recommended that all Mac OSXS machines be updated to the latest release version 1.2. This update is not available from the web site; a CD must be obtained from Apple.
Looking at the server
After a default installation of Mac OSXS, be sure and check the services that are available on the machine and determine which ones are turned On. If you don’t already have a copy of Essential System Administration by O’Reilly & Assoc., procure one. It will be one of the best computer investments you ever make. This books goes over the basics of system administration for UNIX systems. They cover how to setup a UNIX system and the basics needed to run such a server.
To begin, a command to view actively running processes is ps . This command shows any service or application that is running on the system. The ps command is from Berkley UNIX. Is provides a method to list all processes running on a system, among other information. There are many options for ps, check the man pages for more on the various options. The options I use regularly are -aux, for the command ps aux. This lists all of the processes currently running, the user associated with them, memory and processor usage, and the executable associated to the process among other information. Below is an example of the ps aux
bash-2.02$ ps aux
USER PID %CPU %MEM VSIZE RSIZE TT STAT TIME COMMAND
root 547 0.4 1.4 38.7M 3.64M ? S 3:04 AppleFileServer /tmp/afpser
petey 3576 0.4 0.4 2.86M 1.04M p2 S 0:00 -bash (bash)
daemon 459 0.0 0.3 4.30M 888K ? I 0:00 -f /System/Library/RemoteAd
root -1 0.0 0.0 4K 0K ? ?W< 0:00 <mach-task>
root 0 0.0 8.1 196M 20.8M ? U 1:31 (kernel idle)
root 1 0.0 0.3 2.29M 660K ? I 0:00 /sbin/init -v
root -1 0.0 8.1 196M 20.8M ? I < 0:00 <mach-task>
root -1 0.0 0.0 0K 0K ? I 0:00 <mach-task>
root 2 0.0 0.1 2.27M 252K ? SW 0:01 /sbin/mach_init -v
root 3 0.0 0.8 4.63M 1.94M ? IW 0:00 /usr/sbin/kern_loader -n
root 65 0.0 0.2 2.28M 404K ? S 0:00 update
root 152 0.0 0.2 6.88M 628K ? S 0:00 nmserver -nonet -secure
root -1 0.0 0.0 0K 0K ? S 0:00 <mach-task>
There are several means by which you can check the services that are started by the system on boot / reboot: the Network Manager application, and the inetd.conf file.
Your first look at the services that are running on Mac OSXS might be from the Network Manager application. The application is found under the Apple Menu -> Computer Settings. From there, with root access, you can turn off and on services.
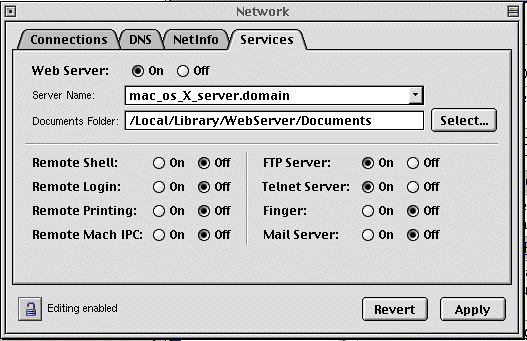
You can also use the /etc/inetd.conf to check on the services. UNIX uses this file to get a detailed picture of the services that will or will not run on the machine. It lists the protocol that is used, by whom it is used, and the application it is to use. To use this approach, enter and execute:
bash-2.02$ more /etc/inetd.conf
#
# Internet server configuration database
#
# @(#)inetd.conf 5.4 (Berkeley) 6/30/90
#
# Items with double hashes in front (##) are not yet implemented in the OS.
#
#finger stream tcp nowait nobody /usr/libexec/fingerd fingerd -s
#ftp stream tcp nowait root /usr/libexec/ftpd ftpd -l
ftp stream tcp nowait root /usr/libexec/tcpd ftpd -l
#login stream tcp nowait root /usr/libexec/rlogind rlogind
#nntp stream tcp nowait usenet /usr/libexec/nntpd nntpd
#ntalk dgram udp wait root /usr/libexec/ntalkd ntalkd
#shell stream tcp nowait root /usr/libexec/rshd rshd
telnet stream tcp nowait root /usr/libexec/telnetd telnetd
#uucpd stream tcp nowait root /usr/libexec/uucpd uucpd
#comsat dgram udp wait root /usr/libexec/comsat comsat
#tftp dgram udp wait nobody /usr/libexec/tftpd tftpd /private/tftpboot
#bootps dgram udp wait root /usr/libexec/bootpd bootpd
##pop3 stream tcp nowait root /usr/local/libexec/popper popper
##imap4 stream tcp nowait root /usr/local/libexec/imapd imapd
#
This is just a short clip of the file. The actual file is much longer.
You can also use this later in configuring security applications.
After you check the services, open the /var/log. This file contains the logs for most of the applications. Review the logs and note the information that they collect. The information that they contain could help you when you need to look for anomalies in system activity.
Services Turned Off
Turning Off any service that is not in use proves a prime starting place in securing your system: running services offer doorways into the system. The following lists those services that are usually unnecessary on the WSU campus network.
Mailserver – Sendmail
Finger
DNS Server
BootP Server – listed in inetd.conf
TFTP Server – listed in inetd.conf
NTP – listed in inetd.conf
Remote Shell
Remote Login
Remote Printing
Remote Mach IPC
You can use the Network Manager application to turn off most services. The application is found under the Apple Menu, under the Computer Settings folder. While you can view the settings as any user, you must have access to root or be root to make any changes from this application. Note that Network Manager does not list all of the services running on Mac OSXS.
Services Turned On
Some services are needed for connectivity or other applications such as serving web pages. If services are needed and running, it is important to know the users of those services. Some of the daemons keep logs; these logs are commonly found under /var/log/hosts.allow restrict file access by hostnames
AppleShare File Services
Macintosh Manager Server
httpd – Apache
Security Options
I found three packages that are of a great help when securing the Mac OS X Server. After removing unused services, there are methods for securing the remaining services running. In each case, a person has taken the time to lay out very good directions for installing and configuring these packages. The original articles can be found on the wonderful Stepwise web site by Scott Anguish.
tcpwrappers – (Jay Swan) while installed by default in Mac OSXS, they are not setup for use. tcpwrappers allow for restricted access and logging of services such as Telnet and FTP. The configuration is straight forward. It uses a configuration file, a hosts.allow and hosts.deny file to manage who can and cannot access the service/system. It can contain individual workstations or entire domains. General setup allows access to WSU clients in general and no one from the outside our domain.
sshd – (Joshua Marker) used in place of Telnet. Secure shell provides an encrypted session between the client and server. Telnet, even with tcpwrapper, is still vulnerable to packet sniffing. The documentation is for setting up and using sshd version1. Work is progressing on getting sshd version 2 up and running. This installation will not only install the ssh daemon, but also the ssh client. In order to use secure shell to connect to the Mac OSXS box, you will need a ssh client. There are a couple of them available for the Macintosh via the web.
xinetd – this is a new package I just learned about a couple of days ago. I have only had a chance to download the article written about it. It seems to be a good package and another security measure to consider if your system is on a network. It replaces tcpwrappers and inetd while also providing rcpmapping facilities. When I have a chance to download, build, and configure it, I will update this page with some results.
portmapper – this is a port of the secure portmapper server. This allows any RPC ports to be remapped so outsiders cannot see which ones are being used. This is a useful option if you are using remote mounting of volumes with NFS.
Logs
Head over to /var/log, in here is where the logs for most applications are kept. These are files of what functions services have performed. While files are useful for keeping information about what happens on and with a system, they can get out of hand quickly. Mac OSXS is setup to archive all logs, it never deletes them. It is up to the System Administrator to go through the logs, collect any relevant information, and purge the remaining logs.
Go through each of the logs and see what information is collected. It could help later on if you need to look for anominalies in system activity. It also helps in determining what information should be kept from each of the logs.
Create a plan for how long logs will be kept. On a busy system the logs can consume quite a bit of room. It would be best to back them up to tape and keep them for some period of time. Check with the Computing and Telecommunications Serives for guidelines on how long to keep your system’s logs.
Accounts
It is important to keep watch over accounts. They are the easiest way into a system. There are some simple steps one can take to help ensure you don’t get bitten by a problem with an account. If you plan on having other people sharing your system, you have to make sure that some ground rules are in place. Let people know up front what you expect from usage of your system – what and what not is acceptable.
The University has standard usage policies for all computer accounts.
First is to make sure that every account has a password. At times, people will create accounts and allow the user to enter a password later, or not assign a password at all. This allows someone easy access onto your system. An example rule for usage could be that any accounts found with a default or no password is disabled.
Second, use permissions to restrict file access. There are many approaches as to approaching assigning permissions. Check Essential System Administration for some of them. The theory behind permissions to to restrict if a user can read, write, or execute any given file. As a System Administrator, one must keep an eye over what permissions are handed out. As quickly as they can protect a file, permissions can be set to let everyone on the system to use the file.
Watch for logins from systems or domains you are unfamiliar with. This could be the first sign of an intruder. Remember to take a rational approach to such a problem, it could be a colleague logging in from a remote site to check on data.
I have pointed one some security measures that can be applied to the Mac OS X Server platform. There are new measures coming over to Mac OSXS on a regular basis. These basic measures can help make your server more secure, protecting your and your client’s data. Use them as a starting point for your own research into UNIX security. As the Mac OS moves to the UNIX world, it is important to know what the system is capable of.
